Information security classification framework (QGISCF)
On this page
Executive summary
The Queensland Government Information security classification framework (QGISCF) supports the Information security policy (IS18). It details how Queensland Government agencies undertake information security classification of their information assets and holdings. This framework uses the QGEA keyword conventions of ‘must’ to denote mandatory obligations and ‘should’ to denote those recommended to agencies.
Information is a valuable resource. Information security classification provides the foundations and structure to understand the relative importance of all government information. Protecting information appropriately from loss, compromise, and misuse in terms of impact to confidentiality (C), integrity (I) and availability (A) is a critical function of government. Both under and over classification of information can have deleterious effects on the operation of government.
Under the QGISCF, Queensland Government information is given a Business Impact Level (BIL) assessment for CIA values, each of which can be a combination of either Low, Medium or High. The BIL levels relate to the information’s importance to Queensland and the damage that could be caused if the information was misused. Security controls are set relative to the BIL assessment.
Requirements
Agencies must:
- identify information assets as required by the QGEA Information asset custodianship policy
- assess the information security classification of information assets and holdings according to business impact to confidentiality (C), integrity (I) and availability (A),
- label medium and high confidentiality information according to impact. The Confidentiality classification labels are:
- OFFICIAL (low or negligible confidentiality impact),
- SENSITIVE (medium confidentiality impact) and
- PROTECTED (high confidentiality impact).
- apply the ACSC Information Security Manual (ISM) at PROTECTED level for high confidentiality information.
- only store or process high business impact level (BIL) information in Australia,
- unless offshoring risks are accepted and signed off by the agency accountable officer (DG or equivalent).
- when receiving classified information from another agency, apply equivalent security controls to those applied by the originating agency.
Agencies should:
- implement the ISM at OFFICIAL:Sensitive level where the agency assesses that it has medium confidentiality impact (SENSITIVE) information.
- apply classification labels to all information to signify confidentiality levels.
- assure themselves that an entity receiving their information can protect the information appropriately.
- document the highest business impact levels and other usage restrictions for their information assets; and
- educate users about responsibilities and handling requirements for handling and use of information over its lifecycle from inception through to disposal.
Implementation
Agencies migrating from earlier versions of the QGISCF should develop a transition plan to move to the current version based on a risk assessment, signed off by the accountable officer or nominated delegate. It is recommended that agencies become fully aligned within 18 months of this document’s publication in the QGEA.
Agencies have the ability to seek exceptions to policy using the QGEA exceptions process.
Introduction
Purpose
The Queensland Government Information Security Classification Framework (QGISCF) supports the Information Security Policy (IS18). It sets the minimum requirements for information security classification, and aligns to national approaches where practical, such as the Australian Government Protective Security Policy Framework (PSPF).
The Information security policy (IS18) states that departments must comply with the QGISCF. We encourage all Queensland Government entities (herein referred to as agencies) to adopt the QGISCF as it represents better practice.
Consistent classification of information helps Queensland Government agencies make more informed and timely decisions about how they should capture, store, maintain, transmit, process, use and share information to best deliver services to Queenslanders. It builds trust between agencies.
This framework provides a process and direction for determining the security classification of information and assets considering three elements of information security risk.
| Information security element | Definition / property |
|---|---|
| Confidentiality | Property of information availability/disclosure to unauthorised individuals, entities, or processes. Risk to information secrecy. |
| Integrity | Property of information accuracy and completeness. Risk to information quality. |
| Availability | Property of information accessibility and usability as required by an authorised individual or entities. Risk of information not being available to the right people at the right time. |
Information security consideration descriptions
National security information
The QGISCF does not provide specific guidance for handling national security information, classified material or systems that are assessed to have confidentiality requirements above PROTECTED. Where an agency has cause to handle such material/systems, it should refer to the:
- Australian Government Protective Security Policy Framework (PSPF)
- Australian Government Information Security Manual (ISM).
Further information and advice is also available from the Queensland Police Service’s Agency Security Advisor, via email qsctc.secretariat@police.qld.gov.au.
Sharing information between agencies
Where an agency shares information with partner agencies, partner agencies must apply equivalent controls. It is good practice to document the business impact levels for information and relevant control expectations between agencies when they share information. In some cases, a classification guide may be useful. Guides give users greater clarity in determining classification levels using specific examples relevant to the subject matter. Further guidance on sharing agreements is available on the ForGov website (search: sharing). The USA Archives document “Developing and Using Security Classification Guides” may also be of use.
Audience
Queensland Government information must be security assessed. This document is intended for the use of employees, service providers and contractors within Queensland Government agencies.
It will be relevant to:
- information owners, information asset custodians and users who are responsible for classification and control of Queensland Government information assets
- users of the information for any relevant and responsible purposes, including sharing or processing the information
- any people who are designing agency services such as business process specialists, service designers and system architects
- business managers, external third parties and service stakeholders
- information security managers and auditors who may assess the security of services
- records managers and others who have responsibility for managing classified information assets over time
- chief information officers and other ICT managers and employees responsible for the supply and operation of information systems.
Classification assessment
Information assets undergo three separate assessments:
- Confidentiality assessment
- Integrity assessment
- Availability assessment
There is not always a direct relationship between confidentiality, integrity, and availability.
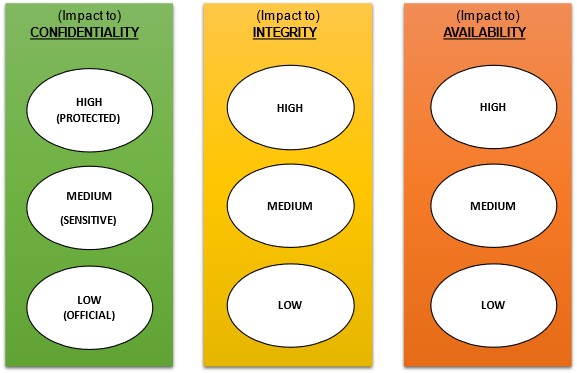
For example, information might have a low or negligible confidentiality requirement and be assigned an OFFICIAL classification level. However, it may well also have a high integrity and medium availability Business Impact Level (BIL) assessment.
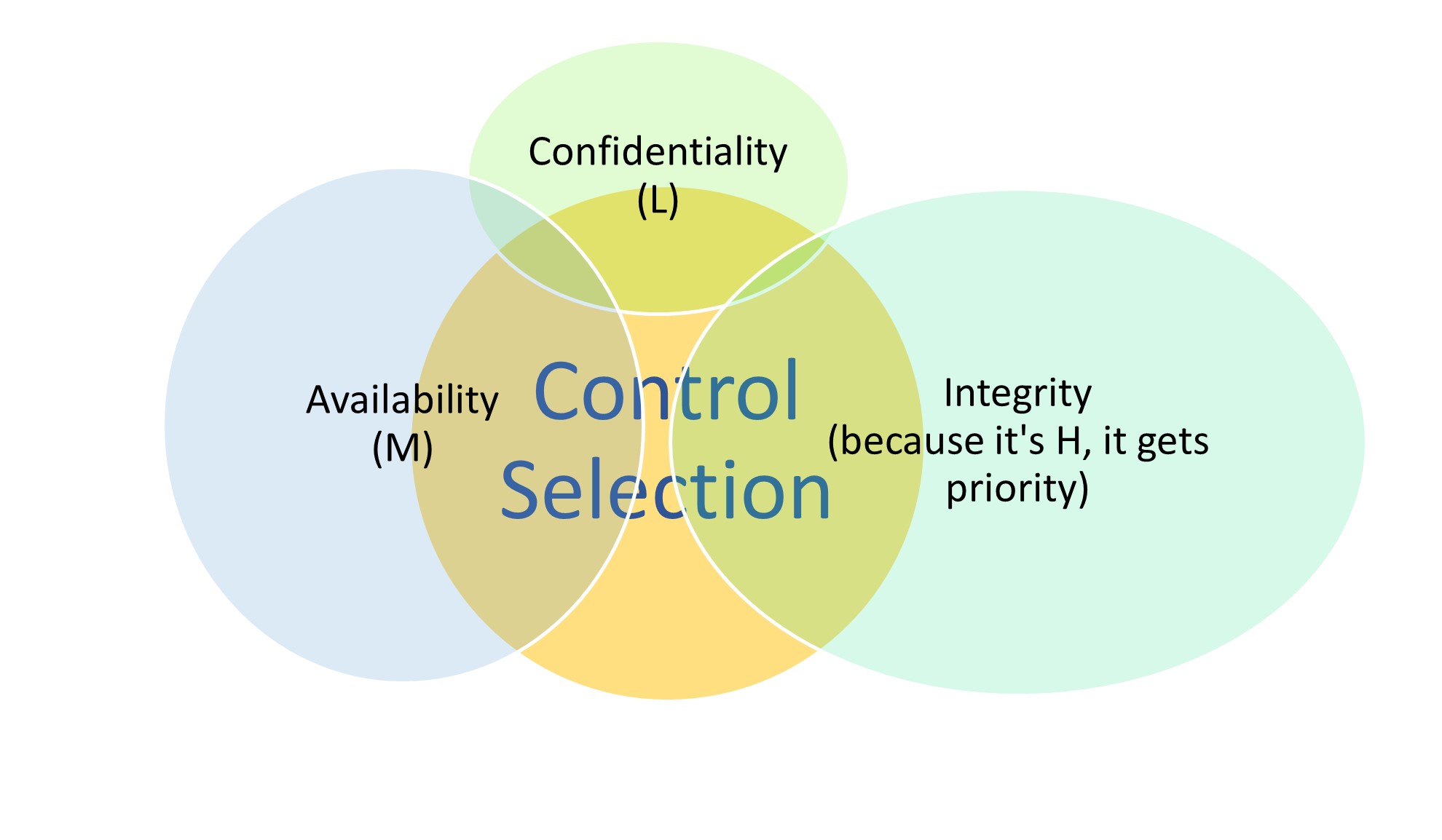 Example: Visualising control prioritisation for a C:L / I:H / A:M
Example: Visualising control prioritisation for a C:L / I:H / A:M
In the above example, the BIL levels are greater than ‘Low’ for integrity and/or availability, the control selection should skew towards mitigations which enhance integrity as much as possible, do not unnecessarily restrict availability, and meet the department’s minimum control requirements for confidentiality.
While BIL labelling is general restricted to ‘confidentiality assessments’, labelling also for integrity and availability can be useful. In the above example you will note a C:L / I:H / A:M notation which indicates for an information assets, it been assessed with the following business impact labels:
- Confidentiality – Low (OFFICIAL)
- Integrity – High
- Availability – Medium
Such notations can be useful when consideration is being given to suitability of controls needed.
Confidentiality assessment
An information security confidentiality assessment examines the impact should the information be inappropriately released maliciously or by accident. A confidentiality label aligned to the business impact can be applied to individual documents or information assets. The information security confidentiality level applied to a document or data element flags how access to the information should be restricted and the efforts that should be made in doing so.
The vast majority of Queensland government information has a low / negligible confidentiality impact and may be labelled OFFICIAL. Security classified information is SENSITIVE (medium confidentiality impact) and PROTECTED information (high confidentiality impact).
Agencies must:
- label medium and high confidentiality information according to impact. The Confidentiality classification labels are:
- OFFICIAL (low or negligible confidentiality impact)
- SENSITIVE (medium confidentiality impact)
- PROTECTED (high confidentiality impact).
- apply the ACSC Information Security Manual (ISM) at PROTECTED level for high confidentiality information.
- only store or process high business impact level (BIL) information in Australia unless offshoring risks are accepted and signed off by the agency accountable officer (DG or equivalent)
- when receiving classified information from another agency, apply equivalent security controls to those applied by the originating agency.
Agencies should:
- implement the ISM at OFFICIAL:Sensitive level where the agency assesses that it has medium confidentiality impact (SENSITIVE) information
- apply classification labels to all information to signify confidentiality levels
- assure themselves that an entity receiving their information can protect the information appropriately
- document the highest business impact levels and other usage restrictions for their information assets
- educate users about responsibilities and handling requirements for handling and use of information over its lifecycle from inception through to disposal.
To assist agencies, business impact level tables have been developed in Appendix A Business impact level tables.
What does ‘apply the ACSC Information Security Manual (ISM) at PROTECTED level’ mean?
The agency applies ISM controls it assesses as applicable for PROTECTED, not necessarily all controls in the ISM.
Agencies can also use the QGEA Exception process and also consider whether information warrants a PROTECTED label on a risk basis.
Confidentiality classification labels
The confidentiality classification labels are considered in relation to the increasing confidentiality business impact, should information be compromised or shared inappropriately.
For legacy information, it may not be practical to label, and agencies may wish to consider Security classification by information asset domain. Further information - Security classification by information asset domain
The classification labels for Queensland Government confidential information are as follows:
| Confidentiality requirement | Confidentiality classification label | Minimum controls |
|---|---|---|
| Low/negligible | OFFICIAL | As per QGEA, and agency risk assessment |
| Medium | SENSITIVE | As per QGEA, and agency risk assessment |
| High | PROTECTED | As per QGEA, and agency risk assessment. ACSC ISM at PROTECTED system security |
| National Security Information (NSI) | Not covered by QGISCF |
To appropriately determine the information confidentiality classification, agencies:
- undertake an information security confidentiality (business impact) assessment to determine the appropriate confidentiality level (OFFICIAL, SENSITIVE, PROTECTED);
- apply security controls which are commensurate with the assessed business impact; and
- select the controls best suited to their risk appetite, business and technology needs, noting the chosen controls must provide sufficient safeguards to adequately protect the information based on the business impact level of the information.
Although not a requirement, agencies may wish to use UNOFFICIAL to allow users to label information that is not work related such as lunch invitations or social club events.
OFFICIAL
OFFICIAL represents most Queensland Government information by volume, but lowest business impact per document if compromised or lost. However, where information is aggregated with multiple information assets such as an ICT Server, the impact of compromise may increase and with it, the necessary controls.
OFFICIAL information is routine information without special sensitivity or handling requirements.
Routine public-sector business, operations and services is OFFICIAL. Most personal information (such as names, addresses and phone numbers) is OFFICIAL.
At the OFFICIAL classification there is a general presumption that data may be shared across government and with stakeholders on a need-to-know basis. Security measures should be proportionate and driven by the business requirement.
Most OFFICIAL information is subject to the Public Records Act and the Right to Information Act 2009. It may also be subject to the Information Privacy Act 2009.
SENSITIVE
The use of SENSITIVE indicates that information requires additional handling care due to its sensitivity or moderate business impact if compromised or lost.
SENSITIVE information must be labelled.
Examples of SENSITIVE information may include:
- government or agency business, whose compromise could cause measurable damage and affect the government’s capacity to make decisions or operate, the public’s confidence in government, the stability of the marketplace etc
- commercial interests, whose compromise could significantly affect the competitive process and provide the opportunity for unfair advantage
- legal professional privilege as defined by legislation
- personal information that people normally consider to be private
- law enforcement operations whose compromise could adversely affect crime prevention; strategies, particular investigations or adversely affect personal safety
Most SENSITIVE information is subject to the Public Records Act.
PROTECTED
PROTECTED information requires the most careful safeguards due to its sensitivity or major business impact if compromised or lost. PROTECTED information assets require a substantial degree of control as compromise could cause serious damage to the State, the Government, commercial entities or members of the public.
PROTECTED information must be labelled and secured whether in digital or analog format.
Most PROTECTED information is subject the Public Records Act.
An example of PROTECTED information may include information which if released would directly lead to death or serious harm.
Special handling markers
Special handling markers (also called Information management markers) may be used where appropriate.
CABINET and National Cabinet
The primary guidance document to support Cabinet and National Cabinet processes, including the handling of Cabinet material, is the Queensland Cabinet Handbook. This document sets out requirements and additional controls for this material.
If a Cabinet document/asset is assessed/marked using the QGISCF and a Cabinet label applied, both the requirements of this document (QGISCF) AND the Cabinet Handbook apply.
Sharing information and the ‘need-to-know’
The ‘need-to-share’ information must be balanced with the ‘need-to-know’ information to perform official tasks. This is a risk decision that can be taken by the agency accountable officer or nominated delegate. Access to some information needs to be restricted because it could harm government interests or the people of Queensland. Applying a security classification to information signals that the agency has assessed the business impact arising from loss of the information’s confidentiality and expects those that access it to secure it appropriately.
Both over-classification and under-classification of information can be detrimental to government.
- over classification of information results in agencies misallocating their resources to spend more money on security than might otherwise be required
- under classification results in agencies exposing themselves to risk because they do not allocate security resources to the information requiring additional safeguards.
All government information must be:
- handled with due care and in accordance with authorised procedures, regulation and legislation
- assessed against the impact that loss of confidentiality would cause to the agency
- released in accordance with the policies, legislative requirements and directives of the Queensland Government and the courts.
Discrete information (unstructured data)
Discrete information, such as documents or emails, may receive an information security confidentiality assessment to indicate the business impact should the information be compromised or made available to the wrong individuals. Agencies should create guidance and procedures to assist employees to classify discrete information correctly.
Information assets (structured data)
For Information assets that are stored in a system, understanding effectiveness of system controls and the ability to securely store confidential information provides an indication of the maximum sensitivity and confidentiality of information that the system is accredited to handle by the agency’s accountable officer. Any assessment must also consider the aggregate sensitivity of the data held in the system.
Australian Government Protective Security Policy Framework
QGISCF is intended to be compatible with the Australian Government Protective Security
Policy Framework (PSPF) and Australian Government Information Security Manual where practical. Queensland has adopted the security classification labels OFFICIAL, SENSITIVE and PROTECTED to align with the federal government approach.
Like the PSPF, the QGISCF considers information that is labelled SENSITIVE or PROTECTED as security classified information.
Information asset confidentiality control summary
This section contains summary details of the controls relevant for the various levels.
OFFICIAL
Information with a ‘low’ or ‘negligible’ confidentiality business impact level Majority of government information. Should be labelled OFFICIAL | OFFICIAL information is routine information without special sensitivity or handling requirements. Compromise may cause limited damage to national security, government agencies, commercial entities or members of the public. The unauthorised disclosure or compromise of OFFICIAL information assets may undermine public confidence in Government operations. OFFICIAL information has confidentiality requirements, unless it is being published. Assets should be marked with this classification level so that it is known that an assessment has been made. Information assets which may not be assessed in a timely manner and do not have a default domain classification established may be best marked as OFFICIAL. Store, handle, archive and disposal
For minimum requirements refer to QGAF and Data Encryption Standard The chosen controls must provide sufficient safeguards to adequately protect the information based on the confidentiality level of the information |
SENSITIVE
Information with a ‘medium’ confidentiality business impact level requiring additional care in handling Must be labelled SENSITIVE | SENSITIVE information requires additional handling care due to its sensitivity or moderate business impact if compromised or lost Store, handle, archive and disposal
For minimum requirements refer to QGAF, Data encryption standard and ISM The chosen controls must provide sufficient safeguards to adequately protect the information based on the confidentiality level of the information. |
PROTECTED
Information with a ‘High’ confidentiality business impact level. Green folder, yellow stripe
Preparation and handling Markings Distinct markings on document or information asset. Centre of top and bottom of each page, in capitals, 5mm (20 point) bold and red if possible. SCI Register Desirable. | The most sensitive Queensland Government information. Information with a ‘High’ confidentiality business impact level, whose compromise could cause actual significant damage to the State, the Government, commercial entities or lethality to members of the public or employees. For instance, compromise could directly endanger individuals’ lives. Store, handle, archive and disposal
Refer to QGAF and Data encryption standard *This means that agency applies ISM controls it assesses as applicable for PROTECTED, not necessarily all controls in the ISM. Agencies retain the QGEA Exception process and can also consider whether information warrants PROTECTED label. |
Integrity assessment
Information integrity refers to how well the information reflects its underlying subject. ISO/IEC 27000:2018 defines integrity as the ‘property of accuracy and completeness.’ Integrity attacks include unauthorised insertion, deletion, or modification of data or agency information such as emails, employee records, contracts, financial records, and customer data.
Information integrity may be compromised by accident or by a (semantic) attack. Such attacks can be especially destructive against financial systems (e.g. Fraud), IoT and SCADA. With the rise of the Internet of Things (IoT), information integrity, including data quality, will be an increasing concern.
Example integrity impact
An organisation maintains a list of widget quantities stored in its warehouse. The information integrity of the list relates to the accuracy and completeness of the list relative to the number of actual physical widgets held in the warehouse.
Following an assessment of business impact levels for the list. The list is assessed to have a ‘high’ integrity BIL requirement. Because of the ‘high’ BIL, the organisation identifies controls which ensure that when audited during the annual physical stock take, the list of widget quantities is highly accurate and complete.
The business impact of inadequate information integrity may differ for different information assets. Inadequate information integrity for financial information will almost certainly have significant financial and/or legal consequences. On the other hand, inadequate information integrity in an email distribution list may only result in inconvenience and slight embarrassment depending on the content of the email.
The integrity level of ‘low or none’, ‘medium’ or ‘high’ should describe the business impact given a harmful event where inappropriate or unauthorised changes have reduced the integrity of the information. The higher the integrity requirement, the more control should be implemented to safeguard information against inappropriate or unauthorised change. Agencies must only store or process high business impact level (BIL) information in Australia unless offshoring risks are accepted and signed off by the agency accountable officer (DG or equivalent)
The outcome of information security integrity assessment should be an indication of the business impact should the integrity of information be compromised. Information integrity levels are determined by the agency business needs, but at a minimum, information should be stored, handled and disposed of in accordance with the Public Records Act and Right to Information Act 2009 (RTI Act) in anticipation of the Information Privacy and Other Legislation Amendment Act 2023 (IPOLA) amending the RTI Act to also cover applications to amend personal information. Other specific legislation, such as the Information Privacy Act 2009 (Qld) and financial accountability regulations may also create information integrity requirements for agencies.
To assist agencies, business impact level tables have been developed in Appendix A Business Impact Level Tables
Availability assessment
For information to be useful and serve the organisations purpose, it must reliably be available when it is needed and, in a form that is able to be consumed by users. Information availability refers to how accessible information is for an intended user or audience at the time the information is required.
Agencies must determine the availability requirements of information that they own and manage and the business impact if the information is not available to the right people or systems at the right time.
Example availability impact
Inadequate information availability of a patient’s electronic health record can have significant impacts to a clinician’s ability to deliver quality health care. In an emergency department, the information needs to be available to clinicians within a short time of being required. The information likely needs to have a High availability assessment. The same information, where it is accessed within a billing system, may have a Low availability requirement. In these two cases, the same information will necessitate different control selection because of the different risk context in the two settings.
The outcome of Information security availability assessment of ‘high’, ‘medium’ or ‘low’ is based on the business impact should the information availability be compromised. Information availability assessment levels are determined by the agency business needs. Agencies must only store or process high business impact level (BIL) information in Australia unless offshoring risks are accepted and signed off by the agency accountable officer (DG or equivalent)
Information availability can be compromised because of both human directed (intentional) and non-directed (unintentional) events.
Unintentional events include failure of equipment due to human error, lack of maintenance or a natural occurrence such as a cyclone.
Intentional attacks, such as denial of service attacks cause disruption of normal functioning of information systems, leading to availability compromise over varying timescales.
Agencies should assess the risk that loss of information availability might cause damage to the organisation and consider whether specific controls are warranted. In many cases, planned and tested business continuity and disaster recovery processes will provide significant mitigation to information availability risk, however, where information is assessed to have a high availability impact, there may be a need for additional controls or approaches to ensure information is available to the right people and systems within the time tolerance required.
To assist agencies, business impact level tables have been developed in Appendix A Business impact level tables.
Information security assessment process
It is necessary to ensure that the information security assessment is a living process, that is, information security needs to be periodically and regularly reassessed as part of the Information Security Management System (ISMS).
Each of the steps identified below is expanded in more detail in the following sub-sections.
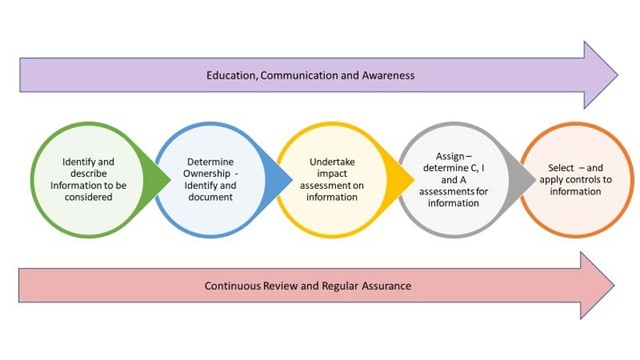 Information security assessment process
Information security assessment process
Identify information
Agencies must identify all information assets that they hold.
The Information asset custodianship policy states the Queensland Government will identify its information assets and assign appropriate custodianship roles and responsibilities to ensure these assets are managed throughout their lifecycle.
Information assets can be documents, electronic messages, a row in a database (or the database table itself), collections of metadata, or a table or figure within a document. An information asset may hold information in multiple formats or media types.
Information assets can be identified by a range of agency processes, including during application of the Digital and ICT strategic planning framework.
In some cases, it may be prudent to logically segment an information asset to be able to assign different business impact levels to the information it contains. Segmentation is discussed further in the appendices.
Determine the owner of the information
All agency information must have an owner as per the Information asset custodianship policy.
Ownership of an information asset or discrete segment of information must reside with only one individual with authority to make decisions about how the information should be handled.
Information ownership must be documented and kept current.
Information ownership may be delegated by the accountable officer (agency head) on a risk basis.
The information owner is responsible for establishing the overall confidentiality, integrity and availability assessments of their information.
The information owner may delegate the day-to-day authority (custodianship) for maintaining information asset controls which must be clearly documented in line with IS44. This delegation can go to a system owner who will need to understand the information asset BIL assessment, particularly where multiple information assets with multiple owners reside in a single system.
Undertake business impact level assessment and assign C I A levels
Using the agency’s business impact levels, information must be assessed to determine confidentiality, integrity and availability levels.
Other agency, regulatory or legislative issues including those arising from the Public Records Act, Right to Information Act 2009 (QLD) and Information Privacy Act 2009 (Qld) may also influence the impact assessment of the information and need to be considered at this point.
Select and apply controls
Appropriate controls must be applied to ensure that safeguards are applied to information assets commensurate with the assessed security classification levels. In some cases, the controls are mandated (e.g. high (PROTECTED) confidentiality information), but in most cases, agencies are encouraged to identify suitable better practice control sets from reputable sources such as ASD/ACSC, ISO/IEC 27002, NIST or ENISA that meet their needs on a risk basis.
Ongoing activities
Continuous review
As environments and circumstances change, information owners should review BIL assessments to ensure controls remain appropriate. The impact from loss, compromise, or damage, and impact to integrity or availability to information may reduce or increase over time.
The decision to change the business impact level for information rests with the information owner.
De-identification, aggregation and redaction techniques can be used to support proactive information release under the Right to Information Act 2009 (QLD) and Information access and use policy. However, care and expertise are required to ensure these are effective and do not introduce risk.
Due care is required to ensure privacy is preserved with data derived from information about individuals.
Assurance
The information security assessments across C I A are determined by the Business Impact Level (BIL) of the information asset. This also contributes to understanding the level of controls needed in systems where information assets are stored. In turn, the BIL guides the level of assurance that should be sought by the organisation relative to the assessed information.
At higher business impact levels, more robust assurance should be sought by the business.
More detail is provided in the Information security assurance and classification guideline.
Education and awareness
The ongoing education and awareness of all employees regarding the importance of classifying information is critical to the success of the overall agency security environment.
Agencies should ensure that all employees have a clear understanding of the agency information security classification policies and procedures, their responsibilities, and principles. Employees who create, process or handle SENSITIVE and above classified information assets should be trained in how to assess and handle classified information.
Education and awareness programs will likely vary across an agency and between agencies and depend on the type of work and types of information assets dealt with.
Information owners and custodians should be given assistance to understand their roles and responsibilities.
Guides to help employees work through the assessment and classification process should be developed. These are of use where information security assessment is not routinely part of an employee’s duties with agency specific examples used to assist.
Business impact levels
Putting it all together
Information security assessment has traditionally been an assessment of the confidentiality of an information asset. Whilst emphasis is legitimately placed on the determination of confidentiality, it is important to also recognise and assess integrity and availability requirements for information on agency operations.
Many Queensland Government information assets also have significant requirements for information integrity and availability. The use of the business impact levels can assist those agencies to classify assets against their integrity and availability, as well as confidentiality. Importantly, where information is found to have high availability or high integrity requirements, agencies should assign proportionate controls based on the BILs.
The information owner must classify the information they are responsible for against the three dimensions of information security.
When determining the correct information security level for an information asset or domain, a range of factors must be considered. Where information assets can be security classified according to legislation, regulation, policy, contractual or other pre-determined means, it should be so classified. For example, breach of proper undertakings to maintain the confidentiality of information provided by third parties and breach of statutory restrictions on the management and disclosure of information need to be considered, and these may influence the overall control selection.
Business impact may be affected by information aggregation. Aggregation of information may change business impact against confidentiality, integrity and/or availability of information.
Controls commonly treat more than one risk. Control selection should aim to mitigate the highest impact risks and if possible, more than one area of the C I A triad. In this way, information security adds value and can be balanced more effectively against the needs of the organisation that it serves.
Agencies should have a repeatable and consistent process to identify business impacts of threats to information in their organisation and that this should consider confidentiality, integrity and availability.
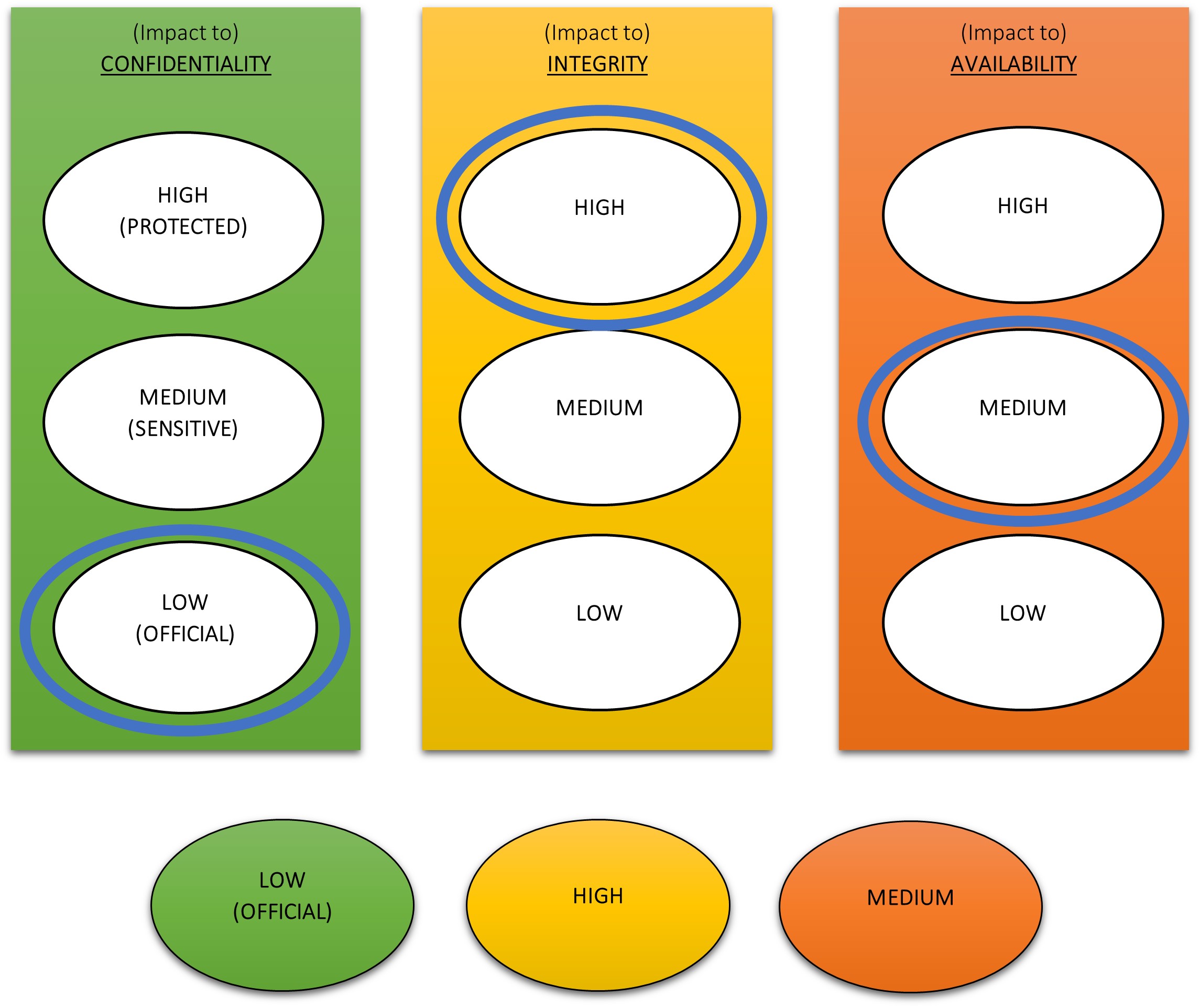
Example assessment of business impacts to confidentiality, integrity, availability levels
This shows an example of an assessment, and in this case the asset has been assessed as high BIL based on integrity, medium availability and low for confidentiality.
The agency should consider existing controls required by the Information Security Policy (IS18), such as Essential 8 controls, and whether those mandatory requirements treat assessed risk to a level that is acceptable to the information owner. If not, the agency should consider additional integrity controls.
Note: Establishing cumulative control sets for CIA high-low may simplify architecture where this needs to be repeated.
For example, an agency may choose to assess risk above baseline controls or create controls standards for classification, as follows:
| Low | Medium | High | |
|---|---|---|---|
| Confidentiality | Assess Baseline Controls | Baseline + Risk Assess need for any additional agency controls | ACSC ISM. + Risk Assess need for any additional agency controls |
| Integrity | Assess Baseline Controls | Baseline + Risk Assess need for any additional agency controls | Baseline + Risk Assess need for any additional agency controls. High Integrity Systems |
| Availability | Assess Baseline Controls | Baseline + Risk Assess need for any additional agency controls | Baseline + Risk Assess need for any additional agency controls. High Availability Systems |
Or, it may be efficient for an agency to create controls standards for some/all of the CIA configurations that reflect the majority of assets:
| Low | Medium | High | |
|---|---|---|---|
| Confidentiality | C Controls Standard Low (ASD ISM OFFICIAL) | C Controls Standard Medium (ASD ISM OFFICIAL: Sensitive) | C Controls Standard High (ASD - ISM PROTECTED Controls, plus agency controls) |
| Integrity | I Controls Standard Low | I Controls Standard Medium | I Controls Standard High |
| Availability | A Controls Standard Low | A Controls Standard Medium | A Controls Standard High |
Appendices
The following are suggested tables of business impacts for Confidentiality, Integrity and Availability which can be customised for individual agency context.
The most effective way of determining business impact levels that align closely to the agency mission is for an agency executive to undertake a process to examine agency information security risk tolerance and appetite. The executive can determine what business impacts their organisation should be focused on. This process can be achieved using the BIL tables in this appendix as a starting point.
The table provides a default mapping between old and new classification labels
Security classification, publishing and Creative Commons licensing FAQ
If an information asset has no security classification label or Creative Commons licence, what process should I follow?
Although the vast majority of government information is OFFICIAL, there is no way of confirming without examining the content.
All information assets must undergo a security classification assessment. A set of information may inherit a classification from the previous QGISCF, in which case, mapping may be used. Domain classification may also be of use where a set of similar information requires classification assessment.
As the Creative Commons licensing process can only be applied to published information, generally only OFFICIAL information that is, or will be, published is a candidate for a Creative Commons licence. However, assessments resulting in MEDIUM or HIGH availability or integrity results may still require publishing.
Therefore, in addition to a security assessment the information will need to go through your department’s publication or information release process.
The security classification helps to understand the confidentiality, integrity and availability needs of the information asset, so that the appropriate controls can be implemented during the preparation and publishing process.
Should the information asset be suitable for publication, a Creative Commons licensing review can be conducted and, if appropriate, a licence applied.
If I receive OFFICIAL:Sensitive labelled information from another party (eg the federal government), how should I treat it?
OFFICIAL:Sensitive information should be treated the same as SENSITIVE information with the same controls and attention to the need-to-know principle.
If an information asset has a security classification (e.g. OFFICIAL, SENSITIVE or PROTECTED) do I need to apply a Creative Commons licence?
A Creative Commons licence can only be applied to information that is published because it implies that the information can be shared publicly and potentially reused. Where an information asset has been published it can be assessed using the Creative Commons licensing review process.
OFFICIAL information is generally suitable for sharing with other government agencies, as there are low/negligible confidentiality requirements. OFFICIAL information that is intended to be published publicly requires further consideration by the department (e.g. under their publishing and information release processes) to ensure the implications are fully understood. However, assessments resulting in MEDIUM or HIGH availability or integrity results may still require publishing.
But what if the information asset has the old security classification PUBLIC but no Creative Commons licence?
Refer the mapping at Appendix B.
Existing information assets that have previously been classified as PUBLIC under the old scheme, can undergo a CC licencing review and be licensed using one of the six CC Licences.
If an information asset already has a Creative Commons licence, what should its security classification be?
If a licence already exists, then it is assumed that the information has been purposefully prepared for publication and is able to be shared with the public under the terms of the cc licence.
As Creative Commons licences generally only apply to information assets that are published, it would be expected that the information would have a classification of OFFICIAL (i.e. the lowest security classification). However, assessments resulting in MEDIUM or HIGH availability or integrity results may still require publishing and thus additional controls to ensure information remains available and unaltered is important. It is best not to guess, and undertake a security assessment just in case anything was overlooked during the decision to publish.
We used to use the old security classification of ‘PUBLIC’ to identify when an information asset can be published – what do I do now?
While a security classification of PUBLIC doesn’t exist, it doesn’t mean you can’t use the term to identify that a decision to publish has been made. More metadata in documents is generally good information management practice. For example, you could add a public label alongside the classification level (eg. OFFICIAL – Public).
Alternatively, you may want to just use the CC licence as an indication – it’s up to your organisation to set the internal procedure.
What are the most common errors seen when classifying information?
Over classification: Information is assigned greater protection than its BIL would require – wasting government resources.
Under classification: Information is assigned lesser protection than its BIL would require – creating risk for the organisation and the classifier.
Misuse of classification: Inappropriate use of classification markings leading to loss of confidence in the classification system by stakeholders including the public at large.
Aggregation: Failure to recognise that a collection of information may have a greater business impact level than its individual elements/records or be of greater value to a malicious attacker.
Can I use additional descriptors for information?
Yes. To support specific business requirements and compartmentalise information, agencies may apply an optional additional descriptor and or metadata to information.
Agencies may decide to use further descriptors when handling, processing and storing their information; however, it should be noted that any additional descriptors may not be understood outside the organisation.
For this reason, information that uses local descriptors may not be handled and protected in the required manner, unless it has been agreed beforehand in an information sharing document such as that outlined in the Information Sharing Authorising Framework.
Should we consider segmenting our information assets by business impact level?
Yes, this is good practice. In cases where information is assessed as having different business impact levels, it requires differential confidentiality, information integrity or availability controls.
Identifying, segmenting and/or segregating high business impact or data from other agency information and applying appropriate controls can be an efficient approach that is superior to raising the security of all information holdings within a single system.
Generally segmenting information so that higher impact information sets are safeguarded from the broader information holdings may work best for Queensland agencies. This approach might be applied where the agency holds relatively small amounts of information that has a higher confidentiality classification, or integrity and availability requirements. Examples include credit card data (PCI-DSS) or information subject to specific legislation, such as the Privacy Act 1988 (Cth).
Should I reclassify information if the business impact has changed?
When information is classified, it is good practice where possible, to determine a specific date or event after which the consequences of compromise might change. Generally it will decrease over time, but not always.
It is important to note that an event may trigger an increase in the confidentiality level of information, for example a human resource form may become ‘SENSITIVE (when complete)’. Alternatively, an archive may become available publicly after a certain number of years. This may change the business impact for the information. Over time, the information may require safeguards for confidentiality reasons, but later it may be that loss of integrity is the primary business impact, or indeed availability.
Some information may require time limited controls because it is under embargo until a specific public policy statement, after which it is published and enters the public domain. If a future date cannot be determined, it is essential to ensure that the date the information assets were created or classified is noted. The date can be recorded either in the document metadata, or the classified asset register if it exists, so that the date be used for future assessment of classification levels, and for right to information purposes.
How should we consider data quality when assessing integrity impacts?
Data quality is an additional information integrity consideration which may be considered in determining business impact. The Australian Bureau of Statistics has released the ABS Data Quality Framework which includes seven dimensions related primarily to information integrity:
- institutional environment
- relevance
- timeliness
- accuracy
- coherence
- interpretability
- accessibility.
The framework can be used for multiple purposes including declaring quality, assessing quality and identifying gaps in data sets.
It is often not practical to individually apply a full security assessment process to every individual document, record, or piece of information in use in an agency. Particularly where there are large quantities of legacy documents.
Agencies should therefore consider an ‘information asset security domain’[1] approach to information security classification.
Agencies may choose to use this approach with legacy information classified under earlier classification schemes using the mappings diagram.
Information asset security domain classifications are not mandatory and should only be established where a logical grouping and standard impact assessment can be identified. It should also be noted that an individual information asset security classification will override any broad domain classification.
An information asset security domain is a grouping of related information assets that share a security classification. The assessment may be based on higher confidentiality, higher integrity, higher availability or a combination of more than one requirement.
Security domains allow a defined level of security assessment to be automatically assigned to assets of the domain. This helps to ensure consistency and reduce owner and user workloads. Domain security classifications must be approved by the information owner/s responsible for the assets that the domain will apply to.
The domain security classification scope will be determined by the ability to group information assets with similar impact assessment results. Often domains will be related to business functions such as human resource management, strategy or procurement functions. Business classification schemes such as those developed for document and records management systems may be useful tools for identifying potential domain security classification areas.
Domain security classifications should be reviewed by agency information owners regularly to ensure they remain appropriate.
Information classified under previous schemes
Agencies may choose to apply a domain approach to legacy information classified under earlier classification schemes using the Mapping between classification schemas.
[1] It should be noted that the information security domain concept being discussed here is not intended to be the same as other domains that may be specified through the QGEA.
There is no restriction on an information owner choosing to label information PUBLIC. Where the information is held on an information system, it will be subject to Integrity and Availability requirements.
PUBLIC is not a security classification level under the QGISCF.
Public information is OFFICIAL information that has undergone an agency authorised publication process to identify that it was suitable to be published. Some of these processes are not security related including relevant copyright identification processes (eg Creative Commons licence). Agencies are encouraged to adopt a label of OFFICIAL:Public to cover both security assessment and decisions where it has been determined the information is suitable for public release.
Agencies need to maintain their own processes to approve information for public release. Some information assets intended for public consumption may have time-limited confidentiality requirements before release (for example, budget papers). In this case, the information should be embargoed, marked and appropriately safeguarded until publication is authorised.
De-identification, de-aggregation and redaction techniques can be used to support proactive information release under the Right to Information Act 2009 and open data goals. However, care and expertise is required to ensure these are effective. Special care is required to ensure privacy is preserved with data derived from information about individuals. The Office of the Information Commissioner Queensland has some useful guidance on privacy and de-identified data.
For further information see the Information access and use policy (IS33).
National security information (NSI) is not a confidentiality classification as different NSI may need different levels of safeguarding.
NSI is any official resource (including equipment) that records information about, or is associated with, Australia’s:
National security information relates to:
- protection from espionage, sabotage, politically motivated violence,
- promotion of communal violence,
- attacks on Australia’s defence system,
- acts of foreign interference and
- the protection of Australia’s territorial and border integrity from serious threats to defence capability.
In some cases, the national security risk may dictate that national interest information requires the same safeguards as national security information.
National interest information is similar in that it comprises official resources (including equipment) that records information about, or is associated with:
- Australia’s international relations, significant political and economic relations with international organisations and foreign governments
- law and governance, including: interstate/ territory relations
- law enforcement operations where compromise could hamper or make useless national crime prevention strategies or investigations, or endanger personal safety
- economic, scientific or technological matters vital to Australia’s stability, integrity and wellbeing, heritage or culture.
The source and holder of almost all national security information is the federal government.
National security information and systems with a confidentiality Business Impact Level above HIGH must be dealt with according to the arrangements outlined in the Memorandum of Understanding on the Protection of National Security Information between the Commonwealth and States and Territories. For electronic information, this will involve the use of specialised hardware and or systems.
Where an agency has cause to handle such material/systems, it should refer to the:
- Australian Government Protective Security Policy Framework (PSPF)
- Australian Government Information Security Manual (ISM)
Further information and advice is available from the Queensland Police Service’s
Agency Security Advisor, via email qsctc.secretariat@police.qld.gov.au
In addition to the above guideline, agency officers responsible for handling national security information will need to meet handling instructions or agreements between their own agency and source federal agencies. This includes:
- physical security
- personnel security
- information security
- security governance.
Familiarity with the Australian Government Protective Security Policy Framework (PSPF) and related documents is also helpful. The federal government operates https://www.protectivesecurity.gov.au as a repository of information related to the PSPF.
It is important to establish some basic business requirements for confidentiality, availability and integrity of the information asset. For example, it is difficult to assess the business impact of a compromise of confidentiality if you are not aware who the authorised or unauthorised group of users are. A patient’s health record is subject to confidentiality requirements contained in the My Health Record Acts (Cth 2012), this means that there is a different business impact if it is shared with a registered medical professional; compared to sharing with a member of the public. Departments should determine the detail this activity should cover. The following questions may assist:
- Who could by default have access to this information (regardless of how they use it) before it creates a negative business impact?
- The Queensland Government aims to be open by default, so it might help to start with the widest audience and narrow from there. For example, could the public have access to the information without a negative business impact to Queensland?
- If yes, everyone could have access.
- If no, then ask could Queensland Government employees have access to the information without a negative business impact?
- If yes, no one outside of the Queensland Government should have access.
- If no, then could everyone in your Agency have access without a business impact? If no, then should everyone in your team have access?
- What is the minimum accuracy required to prevent a business impact? For example, does all information need to be 100% accurate or is 90% accuracy enough to perform an operation without business impact?
- What is the minimum availability required to prevent a business impact? For example, does all information need to be available in real-time 24/7. Or is the information only required during business hours and workdays?
- Are there any legislative or regulatory requirements that must be met?
There will also always be exceptions which may be considered on a case-by-case basis. It is also important that the answers to these questions are revisited regularly as your agency learns more about how (positive or negative) the information is being used
This framework has been developed to align with the following Queensland Government legislation and regulation, Australian Government standards, Australian Standards, and the Queensland Government Enterprise Architecture. Relevant resources are listed below.
QGISCF related information
| Term | Definition |
|---|---|
| Aggregation risk | For a collection of information, the aggregated business impact level may be significantly higher than the individual business impacts of the information |
| Assessment | Assessment is the process of determining the confidentiality, integrity or availability level of information |
| Availability | Information property of being accessible and usable upon demand by an authorised entity. ISO/IEC 27000 The risk to information not being able to be accessed by the right people within a defined time limit |
| Business Impact Level (BIL) | The assessment of predicted effect on an organisation’s ability to operate, resulting from the compromise/reduction of confidentiality, loss/reduction of integrity or loss/reduction of availability of people, information or assets |
| CABINET | The CABINET caveat identifies any information that which has been specifically prepared for the Queensland Government Cabinet or its subcommittees. The Cabinet Handbook outlines controls and procedures for handling of Cabinet material. If a Cabinet document/asset is assessed/marked using the QGISCF and a Cabinet label applied, both the requirements of the QGISCF AND the Cabinet Handbook apply |
| Classification | Information classification is a process in which organisations assess the data that they hold and the level of protection it should be given. In the QGISCF context it is the outcome of the business impact assessments of confidentiality, integrity and availability |
| Classification guide | A document developed using the QGISCF to assist staff to classify information in a repeatable and consistent manner, generally using concrete examples |
| Confidentiality | Property that information is not made available or disclosed to unauthorised individuals, entities, or processes. Further information from ISO/IEC 27000. Risk of unauthorised or inappropriate disclosure or release |
| Control | Measure that is modifying risk. Further information ISO/IEC 27000 |
| Control objective | A control objective is an aim, reason or purpose for which one or more internal controls should be implemented |
| Criticality | The combined impact levels for confidentiality, integrity and availability BILs will provide an indication of criticality of information (High, Medium, Low) |
| Impact assessment | Impact assessment is the process of assessing the probabilities and consequences of risk events if they are realised from the perspective of confidentiality, integrity or availability. The assessment results in a level of high, medium or low for confidentiality, integrity and/or availability |
| Integrity | The information property of accuracy and completeness, Further information ISO/IEC 27000. Risk to information quality |
| ISM | Australian Government Information Security Manual. This document sets out the controls for federal information system |
| Level (Confidentiality) | In the context of the QGISCF: A confidentiality classification level indicates that the information has undergone an impact assessment and level determined allows authorised individuals, entities or processes to gain understanding of its value and, in turn, protect the information at the level deemed to be adequate by the classifier. Queensland has adopted the classification levels of:
|
| National Cabinet | National Cabinet comprises the Prime Minister of Australia (Chair) and the Premiers and Chief Ministers of all Australian states and territories. The Premier represents Queensland on the National Cabinet. The NATIONAL CABINET caveat identifies any information that which has been specifically prepared for National Cabinet or its subcommittees. If a Cabinet document/asset is assessed/marked using the QGISCF and a Cabinet label applied, both the requirements of the QGISCF AND the Cabinet Handbook apply |
| NSI | National Security Information (NSI) relates to:
|
| NTSAF | Queensland Government Network Transmission Security Assurance Framework. The Data encryption standard supersedes the Network Transmission Security Assurance Framework (NTSAF) |
| OFFICIAL | Queensland Government information related to the agency’s business. OFFICIAL is not an information classification |
| PSPF | Australian Government Protective Security Policy Framework |
| PROTECTED | This Security Classification Label is only applied to information with a confidentiality business impact assessment of HIGH. All PROTECTED Information must be labelled and risks to loss or compromise must be considered. PROTECTED is an information classification |
| QGAF | Queensland Government Authentication Framework (part of IS18) |
| Risk | The effect of uncertainty on objectives (ISO 31000). The outcome of a risk event can be either positive or negative. The management of risk is the coordinated set of activities and methods that are used to minimise that uncertainty to acceptable levels. The purpose of risk management is to create and protect organisational value |
| Risk appetite | Risk appetite is “the amount and type of risk that an organization is prepared to pursue, retain or take.” It represents a balance between the potential benefits of innovation and the threats, that change inevitably brings |
| Risk tolerance | The amount of certainty that an organisation allows for a particular risk event. i.e. low tolerance requires high control |
| Semantic attack | A semantic attack is one in which the attacker modifies information in such a way that the result is incorrect, but, in their ideal, looks correct to the viewer. Social engineered semantic attacks manipulate human users’ perceptions and interpretations of computer-generated data to obtain valuable information |
| SENSITIVE | Security classification label SENSITIVE It indicates that information has received a confidentiality business impact assessment of MEDIUM. Equivalent to SENSITIVE in the QGISCF 2018 Equivalent to OFFICIAL:Sensitive in the federal PSPF |
| Threat | Potential cause of an unwanted incident, which may result in harm to a system or organisation. Further information ISO/IEC 27000. A source of harm |
| UNOFFICIAL | A label used for marking information. UNOFFICAL is not a classification label or dissemination limiting marker (DLM). UNOFFICAL information is information which has no relationship with official activities, such as personal correspondence. This information does not form part of official duties. UNOFFICAL may be used to identify information that is incidentally resident on Queensland Government Information Systems (eg Email) |
| Vulnerability | Weakness of an asset or control that can be exploited by one or more threats. Further information ISO/IEC 27000. A flaw, bug or misconfiguration that can be exploited to gain unauthorised access to a network or information |