Digital identity and verifiable credential policy framework
Purpose
The Digital Identity and verifiable credential (DIVC) policy framework is an iterative document that describes the policy domains that need to be discussed to effectively deliver a seamless Queensland Government digital identity and verifiable credential ecosystem.
This document will introduce the policy topics/domains under consideration and provide a definition of each domain. This document is intended to be an evolving policy framework that will be iterated as the policies are developed. It should be used primarily as a reference model to understand the breadth and scope of the policies being considered and delivered. It is acknowledged that the framework is incomplete and will be iteratively developed. As such, if the policy or framework is changed or if any supporting documentation is developed, this will trigger a full formal review.
What is a policy framework?
A policy framework provides a reference model that frames the scope of policy topics/domains that require positions or agreements to affect or enable DIVC service offerings in Queensland.
In practice there will be one policy per domain and it will stipulate and reference the appropriate legislation, standards, guidelines and procedures that underpins the policy domain.
Why do we need it?
A policy framework allows authorising bodies to understand the overall scope of the policy questions that need to be answered to ensure effective participation and delivery of services. This includes the management of the ecosystem, it’s enabling systems and processes. The framework also provides transparency on the key policy areas that require discussion, co-design and agreement. Policy work can also go down rabbit holes and having a policy framework will help advisors, steering committees and the Queensland Government to focus on the right policies to ensure better service delivery outcomes.
Scope
This document is not a policy in and of itself, but to provide a succinct definition and scope of the policy domains that will be required to deliver a robust, scalable, secure and privacy preserving DIVC. This document should be used largely as a reference model for the policies that are being developed to support the delivery of DIVC services in Queensland.
Digital identity and verifiable credential policy domains
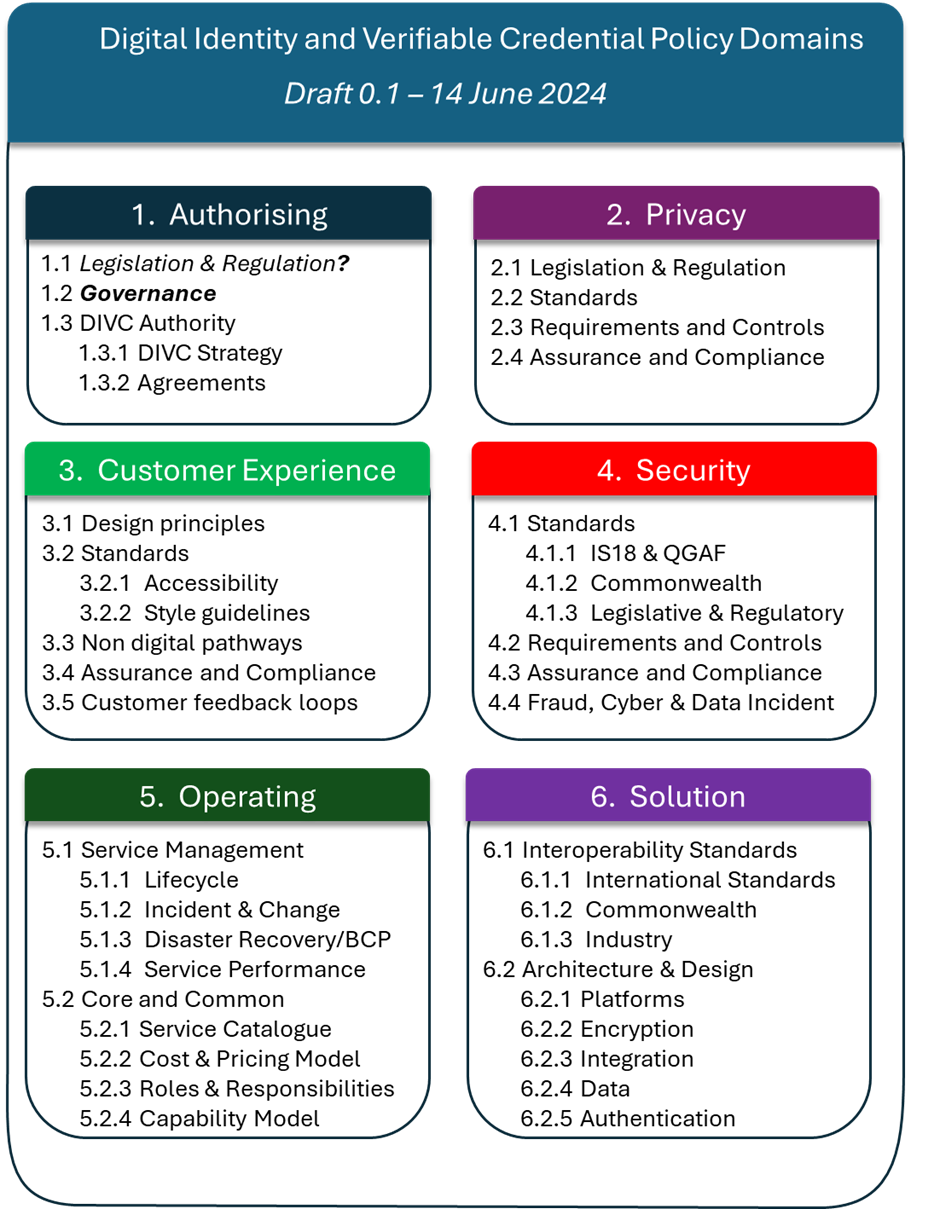
Figure 1 shows the scope the proposed policy domains
1.0 Authorising
The authorising instruments that will support decision making, direction setting and agreements between Queensland Government departments and those leading, steering, governing, delivering DIVCs.
1.1 Legislation and regulation
Legislation or regulations that has or will be enacted to support DIVCs in Queensland.
1.2 Governance
Internal authorising environment of Queensland Government that helps determine direction, priority, agreement, risk management and investment of DIVCs.
1.3 DIVC authority
The contractual agreements between Queensland Government departments and also other jurisdictions (e.g. Commonwealth under the Digital Identity Act 2024) that define the scope of services being delivered and the agreed policy positions that have been agreed to for the delivery, management and support of the in-scope agreed services.
1.3.1 DIVC strategy
The Digital Identity and verifiable credential strategy, principles, roadmap and commitments.
1.3.2 Agreements
Inter-agency and inter-jurisdictional agreements that make up the DIVC ecosystem. The intention is to ensure that legislation and agreements that affect Queensland policy and service delivery are adequately documented and understood.
2.0 Privacy
The necessary policies that ensure the DIVC deliver privacy by design. It covers:
- necessary legislative and regulatory requirements that are required to be met
- standards used to ensure the consistent protection and applied approaches to privacy
- documented agreed controls and procedures that will support privacy by design; and
- necessary assurance activities to ensure agreed policies and controls documented are complied with.
2.1 Legislation and regulation
The current and proposed legislation and regulation that Queensland Government will adopt for its DIVC to ensure privacy by design.
2.2 Standards
The national and international standards that will be adopted to support privacy by design for DIVC.
2.3 Requirements and controls
The privacy requirements of DIVCs and the controls applied to meet those requirements.
2.4 Assurance and compliance
The assurance and compliance activities required to be undertaken to ensure that the DIVCs affectively apply the necessary controls to ensure a privacy by design.
3.0 Customer experience
The documentation of how DIVC’s are implemented in a way that enhances and supports seamless customer experience. This includes ensuring that there are diverse pathways for customers not wanting to have a DIVC and also ensuring the delivery of DIVCs take into consideration accessibility requirements.
3.1 Design principles
The design principles that DIVC services will be adopted to ensure that Queensland customers are provided a seamless and accessible user experience.
3.2 Standards
National and international standards that need to be adopted to maintain accessibility and usability of DIVCs
3.2.1 Accessibility
The adoption of International, national and state standards that ensure that DIVCs are accessible and do not disadvantage the vulnerable in our community.
3.2.2 Style guidelines
These are style guidelines that ensure a consistent user experience and provide confidence to users of Queensland DIVC services.
3.3 Non-digital pathways
While the bulk of policies here are to support the use of DIVCs, not all Queenslander’s want or will have access to them. This is about ensuring that there are alternate pathways to services for those not wanting to use a DIVC.
3.4 Assurance and compliance
The assurance and compliance requirements required to be undertaken to ensure that the DIVC systems are accessible and have non digital pathways for service delivery.
3.5 Customer feedback loops
To ensure that customer feedback on those using both non-digital pathways for identity and credentials as well as those with DIVC are effectively listened to and where possible resolved. Key issues that affect accessibility, equity of access and misuse/fraudulent use of services should have escalation pathways to ensure privacy, security and accessibility of services.
4.0 Security
The standards, security controls and requirements, assurance activities as well as procedural requirements to protect the system and deal with fraud, change and incidents that occur through the delivery of the DIVC. This will form the basis of the Information Security Management System (ISMS) policies, controls and compliance activities.
4.1 Standards
The security standards that will be adopted by the DIVC to protect the ecosystem and be compliant to national and regulatory security requirements.
4.1.2 Information security policy (IS18) and Queensland Government authentication framework (QGAF)
The standards for information security management that will be used by DIVC providers and relying parties. In Queensland this falls under the Information security policy (IS18) and the Queensland Government authentication framework (QGAF)
4.1.3 Commonwealth security standards
While most Commonwealth solutions refer to the 2700X and NIST security controls, there are other specific security postures adopted (e.g. data sovereignty) that are specific requirements. This will identify which of those policy directions will be applied. This includes the Protective Security Policy Framework (PSPF)[1], Information Security Manual (ISM)[2], Gatekeeper[3], National Identity Proofing Guidelines (NIPG)[4] and the Digital Identity Act 2024[5].
4.1.4 Legislative and regulatory standards
The legislation and regulations that the DIVC may be required to be compliant to and other statutory considerations in the management and delivery of its service.
4.2 Requirements and controls
While 4.1 Standards identifies the standards and relevant Commonwealth security standards, legislative and regulatory requirements, this section focuses on the specific security controls that will be applied to DIVC providers. This will list the security requirements as identified under 4.1 and subsections and provide transparency and risk postures of the controls that will be applied.
4.3 Assurance and compliance
This takes into consideration of 4.1, 4.2 and 4.4 as part of its assurance and compliance activities. This will also include the certification requirements of the system to ensure DIVC providers and relying parties are compliant with all its security requirements.
4.4 Fraud, cyber and data incident management
These are a combination of policies and procedures that are used to prevent, mitigate and manage fraud, cyber and data incidents that may occur in the DIVC ecosystem. This will be linked also to 1.2 Governance to ensure effective oversight and authority to act is clearly defined during those incidents or to approved preventative and risk mitigating measures.
5.0 Operating
The operational policy domain focuses on service management of DIVCs, operating model and defining the products and services being delivered in Queensland. This includes the transparent costing and pricing model used to fund those services. The operating model also articulates the roles and responsibilities of those that operate DIVC services.
5.1 Service management
Service management is the overall management of the DIVC services in Queensland. This includes configuration, incident and change management of the DIVC platforms. This will also include the disaster recovery and business continuity protocols and controls to ensure the performance of the DIVC services are optimal.
5.1.1 Lifecycle management
The lifecycle management of the solution as defined in section 6.0 Solution and the services they enable under 5.2.1 Service catalogue to ensure that the end-to-end platforms and services that are enabled by those solutions operate effectively and efficiently.
5.1.2 Incident and change management
This will have overlap on 4.4 Security fraud, cyber and data incident management and 5.1.3 around disaster recovery (DR) and business continuity planning (BCP). This will document the incident and change management practices, responsibilities and controls to effectively deal with those occurrences in the DIVC.
5.1.3 Disaster Recovery (DR) and Business Continuity Planning (BCP)
The DR and BCP plans processes and approaches to ensure in the event of realised risks, service failure and unforeseen circumstances that jeopardises or makes the system non-functional, there are effectively plans to ensure business and service continuity and recovery.
5.1.4 Service performance
The documented service performance baseline and agreed performance requirements and service level agreements that DIVC providers operates to. This could include service levels as agreed to by managed service providers as well as performance requirements offered to participating jurisdictions.
5.2 Core and common
Describes the services, processes, roles responsibilities and financial management components of delivering the DIVC services that are core and common.
5.2.1 Service catalogue
The list of services and products and in some cases managed processes that are provided by Queensland Government DIVC providers. The service catalogue is tied also to 5.1 Service management where identified services are actively managed.
5.2.2 Cost and pricing model
The transparent costs and pricing model of the services in 5.2.1 Service catalogue and how they are calculated.
5.2.3 Roles and responsibilities
The roles and responsibilities of those managing the services and the systems that enable them.
5.2.4 Capability model
The capability model provides an agreed roadmap of increasing resources, in particular people and systems in line with growth of system uptake and expansion of products and services of a DIVC service provider. The focus of this model is to ensure scalability and sustainability of the platform as it grows, and innovation is likely to also require system and operating adjustment and investment.
6.0 Solution
The solution defines the architectural scope, system design and the interoperability requirements of DIVCs.
6.1 Interoperability standards
The standards that the DIVC will adopt to ensure that the systems across Queensland (especially relying parties) can successfully scale and interoperate to ensure seamless customer and service experience.
6.1.1 International standards
The international interoperability standards the DIVC providers will be adopting to ensure a seamless customer experience and ensure consistent integration between DIVC systems and end points within Queensland and industry.
6.1.2 Commonwealth
The interoperability standards that the Commonwealth has prescribed that are being adopted as part of DIVC solutions. This could include aspects of the Digital Identity Bill, National Identity Proofing Guidelines (NIPG) and other interoperability standards DIVC providers will include.
6.1.3 Industry
The industry interoperability standards that will be adopted by the DIVC providers to ensure acceptance by industry sectors and ensure whole of economy adoption.
6.2 Architecture and design
This defines the scope of platforms, integration requirements, data models, authentication methods and encryption approaches that will be applied by DIVC providers and participating departments and commercial providers.
6.2.1 Platforms
This will document the digital systems including managed platforms used to enable and support the DIVC ecosystem.
6.2.2 Encryption
The encryption standards and approaches that are used to protect data, integrations and platforms across the DIVC ecosystem.
6.2.3 Integration
The integration standards and approaches that connect systems and manage the movement of data within the DIVC ecosystem.
6.2.4 Data
The data models for credential types and identities that will be used on the DIVC. This will also include data management practices and data protection requirements.
6.2.4 Authentication
The standards and protocols used to affect authentication across the DIVC including the level of assurance applied to different authentication approaches.
Appendix A: Connected QGEA policies
The following are a list of QGEA policies that will be reviewed as part of the development of DIVC policies. The intention is to reference existing policies and standards where practical rather than write new policies in similar domains.
Existing policy | DIVC Domain relevance | Commentary |
|---|---|---|
3.3 Non digital pathways | Ensure a consistent experience across multiple channels when using DIVC. | |
2.3 Privacy requirements and controls 4.3 Security assurance and compliance 6.2.4 Data | Identity attributes are often use to establish a customer account are captured. | |
6.1 Interoperability standard 6.2.2 Encryption | DIVC require end to end encryption to ensure data and transport protection. | |
3.2.1 Customer accessibility | Ensuring that DIVC complies with accessibility requirements for a digital service. | |
5.1 Service management | Identity solutions use Domain names and reverse name spaces for certifications, hosting data and identity objects. | |
5.2.1 Service catalogue 6.1 Interoperability Standard | Verifiable credentials generate electronic signatures for each credential. This can be reused on a range of customer use cases. | |
6.2 Architecture and Design | This has a traditional identity framework for federated identity and does not cater for distributed forms. | |
6.2 Architecture and Design | This has a traditional identity architecture for federated identity and does not cater for distributed forms. | |
4.4 Fraud, Cyber & Data Incident Management 5.1.2 Incident & change 5.1.3 Disaster recovery and business continuity | There will be requirements to deal with incidents related to DIVC. | |
5.1 Service management | Ensure customer information is managed effectively. | |
4.3 Security assurance and compliance | The identity and accompanying attributes are adequately classified. | |
4.4 Fraud, cyber and data incident 5.1.2 Incident and change management | Ensuring that information security incidents complies to existing incident reporting standard. | |
4.1 Security standards | IS18 is the prime security policy in Queensland government with accompanying security standards requirements. | |
2.2 Privacy standards 6.2.4 Data | Services using identity may capture metadata as part of the service. | |
6.1 Interoperability standard | Identities use digital certificates which contain OIDs that are used by relying parties. | |
Principles for the design, development and deployment of mobile apps | 3.1 Customer experience design principles | Take into consideration how identity enrolment and use complies to mobile app design principles. |
4.1 Security standards | QGAF covers levels of assurance and risk assessments on authentication requirements that also determine your assurance levels for your identity. | |
4.2 Security requirements and controls | Ensuring vectors of vulnerabilities are effectively managed. |
Footnotes
[1]Policies | Protective Security Policy Framework
[2]Information Security Manual (ISM) | Cyber.gov.au
[3]Gatekeeper Public Key Infrastructure Framework | Department of Finance
[4]National Identity Proofing Guidelines | Attorney-General's Department (ag.gov.au)
[5]Digital ID Bill 2024 – Parliament of Australia (aph.gov.au) [Will be changed to an Act once in Law]