Remote working guideline
Introduction
Purpose
This guideline provides information and advice for Queensland Government departments as they facilitate remote working arrangements, including working from home. These guidelines are not mandatory and they serve as a guide only. While some information may communicate other relevant mandatory obligations (e.g. legislation), departments are strongly recommended to further investigate these obligations considering their own business requirements and seek legal/expert advice where necessary.
Audience
This document is primarily intended for
- chief information officers (CIOs)/other senior officers who authorise how departmental ICT services, facilities and devices may be used
- human resource professionals
- information management and ICT policy staff
- cyber security staff
- staff who supervise and manage employees.
Scope
This document addresses some of the risks and issues associated with remote working including security, bring your own device (BYOD), information management, privacy, recordkeeping, acceptable use and workplace health and safety considerations.
The terms working from home and working remotely are used interchangeably throughout the document.
Background
There is need for the public service to change the way it does business, particularly the use of flexible working arrangements, including remote working and working from home, where practical.
It is important departments continue to deliver essential services, and where remote working approaches are practical, these should be encouraged.
Not all work is suitable for undertaking remotely, however departments should take all reasonable steps to ensure technology is not a barrier to working arrangements, and this could include thinking about how work and associated processes could be redesigned or reimagined to enable remote working.
Take a pragmatic approach
Departments need to take a pragmatic approach when considering the risks of remote working and are encouraged to develop flexible and practical processes and practices. Departments should consider whether a particular risk has truly increased, or whether similar risks were always present when working in the office.
For example, the risk of unauthorised sharing of confidential information. There is a misconception that working remotely/working from home allows employees to share confidential information with those who should not have access to such information. Unless the workplace has restrictions in allowing mobile phones in the workplace, the reality is that any employee could take a picture of information and share it. Working from home in this instance does not increase nor decrease this likelihood significantly. Instead, it is the employee motivation for doing such things that is the core issue – and as such employee education and awareness is paramount in these situations.
These types of issues are governed under a range of existing legislation and policy such as the Information security policy (IS18), the Use of ICT services, facilities and devices policy (IS38), the Public Sector Act 2022, the Public Sector Ethics Act 1994 and the Code of Conduct for the Queensland public service.
The following sections provide information on the variety of issues that should be considered when facilitating remote working and working from home arrangements.
Duty of care
Departments have a primary duty of care and should do what is reasonably practicable to ensure the health and safety of their employees as they work from their home.
Reasonable steps should be taken to ensure a worker's home-based area meets work, health and safety requirements. Employees who are carrying out work for their employer at home are still covered under WHS legislation. Departments should consider:
- what equipment is required
- the home-based work environment including setup and ergonomics
- job design and workload
- communication and how to stay connected.
Remote working considerations
It is recommended that departments update their security policies to reflect the remote working considerations.
Departments should ensure the training materials relating to remote access policies, procedures and practices are kept up to date, and staff awareness of this subject is regularly refreshed and monitored.
Departments should assess the business requirements for remote working by considering the nature of the duties to be conducted remotely, and the sensitivity of information required to be accessed to perform those duties. An informed decision should then be made on provisioning departmental portable devices or permitting access from non-departmental devices (e.g. BYOD). Additionally, the use of BYOD may be considered as a supplementary option to the departmental portable devices where risks are acceptable to the business in order to drive productivity and business continuity. Where BYOD is allowed, departments should ensure employees have secure access to departmental networks and applications, and consider deploying agentless mobile security solutions where practical.
As mentioned above, a pragmatic, risk-based approach to remote working arrangements is highly recommended. Remote working arrangements can allow the continuation of service delivery and other core services, where situations arise that employees cannot physically go to the office. As such when considering risks of remote working the risks of not being able to deliver services or support service delivery need to also be balanced.
Similarly, the risk of accidental sharing in the workplace, such as employees not locking their computers when away from the desk. The need to continue ensuring screens are locked when away from the computer is still important whether working from the office or from another location.
Security considerations for use of departmental portable devices
In line with the Information Security Policy (IS18), departments should consider the following for staff who use portable electronic devices provided by the department (please note considerations for BYOD are included in a separate section of this document):
- documents should be handled according to their security classification and appropriate controls (on both digital and physical documents) should be applied
- government information should not be downloaded and/or stored on non-departmental devices (e.g. personal computers, phones, USB storage devices etc.), or applications (e.g. personal email or cloud storage accounts)
- departmental portable devices should be appropriately secured by encrypting the device storage and by use of strong passwords and biometric security where possible
- the use of simple pin numbers or screen lock patterns as a sole security protection should not be permitted. The simple rule for secure passwords is “the longer the better” with a mixture of uppercase, lowercase, numbers, and symbols. The Australian government also suggests a paraphrase made up of 4 words that are meaningful but not easy for others to guess (minimum 14 characters in total) can also make a strong password.
- departmental portable devices should be remotely managed to ensure data can be remotely wiped in case of stolen/misplaced devices
- lost or stolen portable devices should be immediately reported to a department’s IT service provider/department so remote access functions or other application credentials can be deactivated or reset if necessary
- departmental portable devices should be physically secured in transit to prevent theft and/or damage. For example, a departmental laptop or phone should never be left in a visible spot inside a parked vehicle or left unattended in a public space
- remind staff about risks of using departmental portable devices in public spaces, and considering social engineering aspects such as shoulder surfing when entering departmental passwords – this includes physical proximity of potential attacker or placements of nearby cameras – use of biometric security is encouraged to minimise this risk
- ensure departmental multifactor authentication tokens are appropriately protected (e.g. keeping physical tokens secured or restricting access to digital tokens by keeping them locked)
- the departmental portable devices are locked automatically after a short period of inactivity and staff are reminded to lock their devices when they are not using them even if they are working from home
- connecting to untrusted Wi-Fi hotspots to access Queensland Government networks, both on personal or government owned devices should be strongly discouraged and blocked where possible – cyber criminals can easily access information in transit over public wi-fi networks and potentially compromise the department’s device.
Some of the recommended use cases for remote network access are:
- using a secure guest Wi-Fi belonging to another federal, state, or local government entity if possible
- using a secured Wi-Fi hotspot created on a Queensland Government smartphone
- considering the use of a departmental cellular data plan either via a built-in modem (available in some tablets and laptops), or via a USB connected cellular 4G/5G modem with a departmental cellular data plan
- using employee’s secured home Wi-Fi internet connection if a VPN technology is used on the departmental device being connected.
Security considerations for use of BYOD
Bring your own device (BYOD) may be considered to increase employee’s efficiency and flexibility as the reality is not every employee is issued with a departmental device.
BYOD can also reduce overhead costs of departments in issuing every person a device.
It is recommended departments take active measures to ensure employees have secure access to departmental networks and applications as much as practical. Employees should not be compelled to work ‘around the system’ (e.g. send documents to their personal accounts or store documents on their personal devices to ensure they get their job done when using the BYOD).
Solutions like mobile device management which install software of every employee’s personal device are not only difficult to roll out and maintain, but they may diminish user’s experience, do not integrate well with cloud solutions and could violate employee’s privacy.
Instead, it is recommended for departments to consider deploying agentless mobile security solutions which protects the data itself, without needing to install anything on an employee’s personal device. The agentless solutions can also offer data encryption which can be used with other solutions such as Office 365.
When using BYOD, it is important that departments strike a balance between the risks of using BYOD and the need to continue delivery and supporting service delivery. In line with the Information security policy (IS18), it is recommended departments:
- ensure a multi-factor authentication is implemented to facilitate access from any non-departmental devices
- consider providing staff with ability to remotely access the department’s ICT environment and applications through use of secured Remote Access where possible. Whilst this option may not be as flexible, if configured appropriately, it could minimise several risks associated with the use of BYOD
- consider implementing an agentless mobile security solution and configure it to block downloading government information onto BYOD (e.g. private computers or phones), and applications (e.g. personal email or cloud storage accounts)
- consider educating staff using BYOD to:
- keep their devices’ operating systems, security patching, anti-virus and applications up to date,
- avoid printing on personal devices unless documents can be stored or disposed securely in line with their classification,
- notify their IT department if the device being used is lost or stolen in order to prevent compromised access to Queensland Government systems and information.
Stay vigilant to cyber attacks
Cyber criminals are opportunistic. They can use particular situations to steal valuable government information and data through email and SMS phishing scams that could compromise Queensland Government networks, systems and data, potentially resulting in a significant disruption in service delivery and the business of government. It is likely these kinds of cyber-attacks and scams will continue and potentially increase. The ways cyber criminals execute an attack may also change and include taking advantage of vulnerabilities related to working from home.
Technical patterns
There are a variety of patterns for applications to be made available when working remotely:
- Secure reverse proxy: Netscaler, F5, Azure AD Application Proxy, etc
- Managed departmental desktop with VPN: complete connection or split tunnel
- Encapsulation and remote presentation: Remote Desktop – Citrix, RDP, VDI, etc.
When systems are designed, they should take into consideration remote access. Departments should have pre-determined patterns for making applications and services available remotely, ideally these should be cost effective, secure, and scalable. An example of this is making a corporate intranet available to work-from-home staff through the activation of Azure AD Application Proxy – this allows multi-factor authentication through any browser allowing a staff member to access the intranet with existing credentials and minimal infrastructure costs.
When making use of VPN services it is strongly discouraged to route all traffic back to the departmental network. This is due to the resulting doubling of traffic on departmental infrastructure due to services such as Office365 being unnecessarily routed via departmental internet links multiple times. This painful lesson has already been learned multiple times by Queensland Government departments and does not need to be repeated, the diagram below depicts the difference.
Without split tunnel:
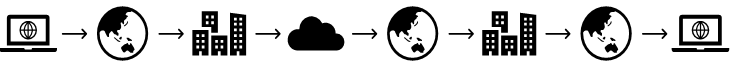
With split tunnel:

It should be noted that defence behind department firewalls is typically not a reflection of modern security practises, as is reflected by the ASD essential eight where corporate firewalls are not listed.
Information management and privacy
When working remotely, all staff should remain aware of the importance of good information management practice. The Queensland Government is increasingly reliant on data and information and everyone who creates, accesses, uses or stores information has a role to play in the effective management of a department’s information. Ensuring staff are trained in their responsibilities, have access to departmental policies and procedures and are actively encouraged to manage their information ensures they are able to implement appropriate information management practices while working remotely.
It is important to remember while working remotely, that departmental information remains subject to a range of legislative requirements including the Public Records Act 2002, the Information Privacy Act 2009, and the Right to Information Act 2009. Depending on the type of information staff are accessing remotely, there may also be departmental specific legislation which dictates how or where that information may be stored, accessed and managed. This information may include original information as well as metadata, transactional records and backup copies. Although staff may not be physically working within a department, they retain responsibility for all aspects of information management related to that department’s information. Further advice on detailed best practice information management can be found on the Information management page on the For Government website.
The protection of personal information collected and held by Queensland Government departments is still paramount and departments must continue to adhere to the Information Privacy Act 2009.
Departments must ensure that employees continue to handle personal information appropriately, even when working remotely. Departments should take into consideration where remote working has resulted in changes to business processes and ensure that privacy issues are considered. Departments may consider limiting the collection, use and disclosure of personal information to what is necessary. Further information on handling personal information is available from the Office of the Australian Information Commission.
Departments should also ensure employees only use approved applications for collaboration purposes. Some unapproved popular video conferencing platforms collect personal data from users such as caller’s location data, operating system, IP address, and what kind of device they are using. It is therefore important to only use the departmental approved system. See also Collaboration Platform (Microsoft Teams) policy.
Similarly, employees should be wary of how they use social media platforms to share their work from home experience. Activities like using video chat and posting pics to social media of home office set ups could inadvertently share sensitive information such as family photos and address details etc. It is always good to be vigilant about what is posted to social media and use features such as blur background of video chats to keep family members personal details and activities secure.
Working remotely can cause challenges from a Right to Information (RTI) and privacy perspective and the Office of the Information Commission has developed FAQs.
Records management
With more staff using remote working options, it is inevitable that decisions will be made outside of normal work processes, impacting the capability to accurately record actions, decisions and rational. It is therefore vital that departments continue to adhere to their recordkeeping obligations under the Public Records Act 2002 and set clear expectations and processes in how records are created, managed and maintained. Queensland State Archives have a range of resources and advice to support Queensland Government agencies with recordkeeping.
If employees are working from home or remotely, it is important to remember that their recordkeeping responsibilities do not change. With more staff using remote working options, you may not be able to access your official business systems, impacting your ability to accurately record actions, decisions and their rationale in the normal way. It is therefore vital that departments continue to adhere to their recordkeeping obligations under the Public Records Act 2002 and set clear expectations and processes about how records are created, managed and maintained when working from home. Queensland State Archives have a range of resources and advice to support Queensland Government agencies with recordkeeping.
Acceptable use (personal use) considerations
When working from home, departments need to provide employees with a range of corporate ICT solutions to enable them to continue to perform their duties, from devices such as laptop computers, to access to networks, technologies and applications (e.g. Office 365)
It is therefore important departments continue to reinforce expectations on the use of government owned ICT services, facilities and devices (as per the Use of ICT services, facilities and devices policy), including expectations on employee limited personal use of these resources. Working from home should provide employees easier access to personal devices to conduct personal activities, however boundaries can be blurred, and employees can easily forget to jump between devices and profiles. As such in remote working situations departments should implement workable practices and reinforce expectations. Importantly, departments should remind employees their use of government owned ICT services facilities and devices must be able to withstand public scrutiny and/or disclosure, and their behaviour must be in accordance with the Public Sector Act 2022, the Public Sector Ethics Act 1994 and the Code of Conduct for the Queensland public service
One practical way is to encourage employees to use separate devices – one for work, and one for personal use, as this is an easy way to set clear boundaries. That way employees can easily use their work device, for work purposes during work hours. Then after hours and during breaks, the employee can use their personal computer for personal activities.
Where employees do not have multiple devices available, departments can encourage employees to create two separate accounts – one for work and one for personal use. This is particularly important if the computer used is a shared family computer and provides an easy way for employees to keep their work and personal activities separate.
Departments should also look into modifying their policies around the use of personal mobile phones – as they will be a communication device employees will use to stay in touch with work colleagues and may be used to access corporate systems. Departments may wish to set parameters around how such devices should be used, particularly from a recordkeeping perspective (e.g. text messaging via personal mobile phone should not be used to record any business decisions). The Public Sector Commission’s Private use email policy has some useful information regarding use of personal devices and accounts for official purposes.
As always, it is extremely important departments ensure their policies and examples of authorised and unauthorised use are updated to reflect remote working situations and all employees are aware of, understand and acknowledge their responsibilities and policy obligations when using government-owned ICT services, facilities and devices.
Workplace health and safety
While working remotely, it is important for departments to ensure the health, safety and wellbeing of their staff. Remote working can be isolating, and departments should ensure managers and employees regularly engage and communicate.
Departments should also work with and empower employees to take responsibility for their own health, safety and wellbeing, including establishing a safe work environment at home. For further information on how to get the best out of working remotely see flexible work on the For Government website.
When establishing and maintaining a safe work environment at home, consider these factors:
- reduce hazards by ensuring areas are free from obstructions and trip hazards (including computer and electrical cords)
- keep equipment safe, well maintained and in good order
- ensure there is enough natural light without glare, reflections, awkward postures or squinting/straining of the eyes
- ensure sufficient airflow levels
- take regular breaks including stretching to assist overall health and posture.
For information about factors to consider, see health and safety for working from home.
Employee communication is essential
Departments should remind employees of the importance of connecting with their managers and colleagues when working remotely. The culture of a workplace is built on communication across and within teams, so it is vital during remote working situations that communication is made a priority.
For more information about communication and staying connected, see flexible work on the For Government website.
Clear and continuous user education and awareness on all the above activities is extremely important to ensure employees understand their obligations when working remotely. It is also important employees can contact their IT department quickly for advice